IDENTITY THREAT DETECTION & RESPONSE
Detect all human and non-human identity threats
Permiso provides comprehensive identity threat detection and response for all human and non-human identities across all of your environments.
Detect account takeover, credential compromise and insider threat in minutes.
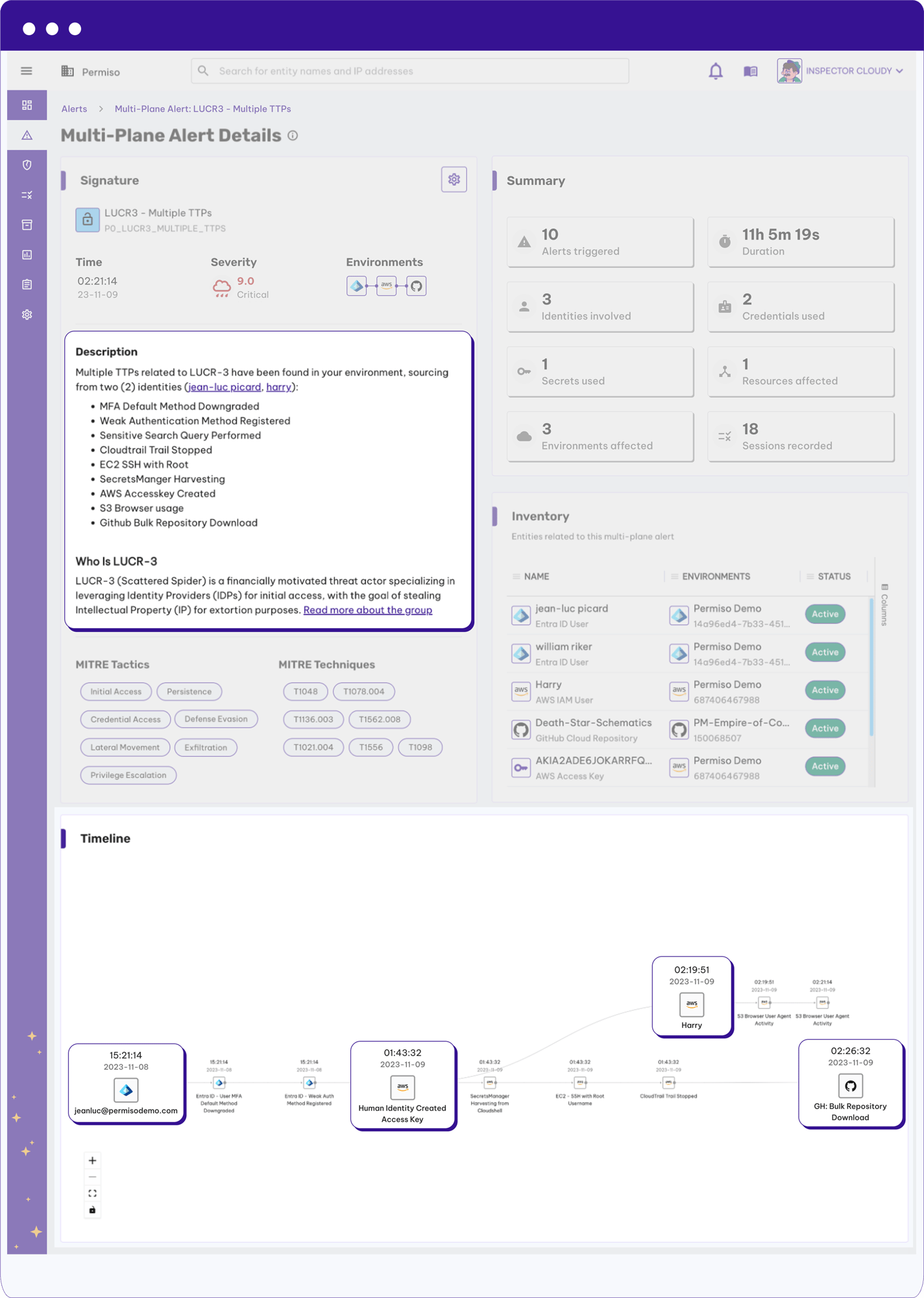


Universal Identity Graph
Comprehensive identity security coverage by stitching all user activity together across identity providers, IaaS, Paas and SaaS environments.
P0 Labs Driven Detection Engine
Protect All Environments
Permiso detects access and behavioral anomalies for environments like AWS, Azure, GCP, GitHub, Slack, Salesforce, and more.
Detect Account Takeover
Account Takeover attacks often go undetected for weeks or months. Whether it's through credential compromise, access anomalies or behavioral anomalies, Permiso’s identity runtime threat detection enables organizations to track all identities, across all of the cloud environments, detecting ATO in realtime.





Prevent Data Theft
Some of the most valuable intellectual property companies have is in the cloud. Whether it's source code, code signing certificates or other sensitive data, threat actors are quick to exfiltrate data out from cloud infrastructure and SaaS environments. Permiso monitors human and non-human identities for access and behavior anomalies in AWS, GitHub, Jira, Salesforce, Snowflake and other critical cloud services that host your most important intellectual property.
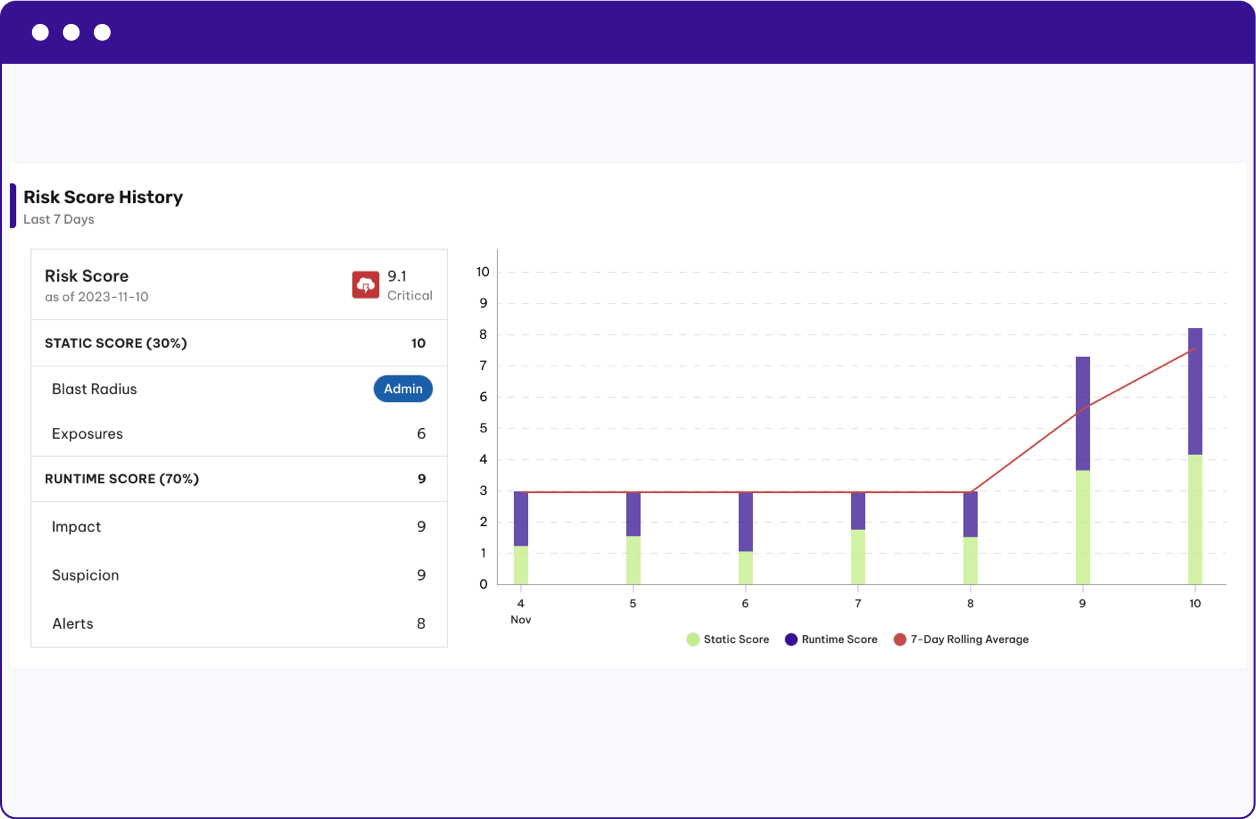
Detect Insider Risk
With Permiso's watchlist capability, protect sensitive data and intellectual property by identifying and mitigating threats from employees, contractors, and other trusted individuals who may be intentionally or unintentionally posing security risks to the organization.
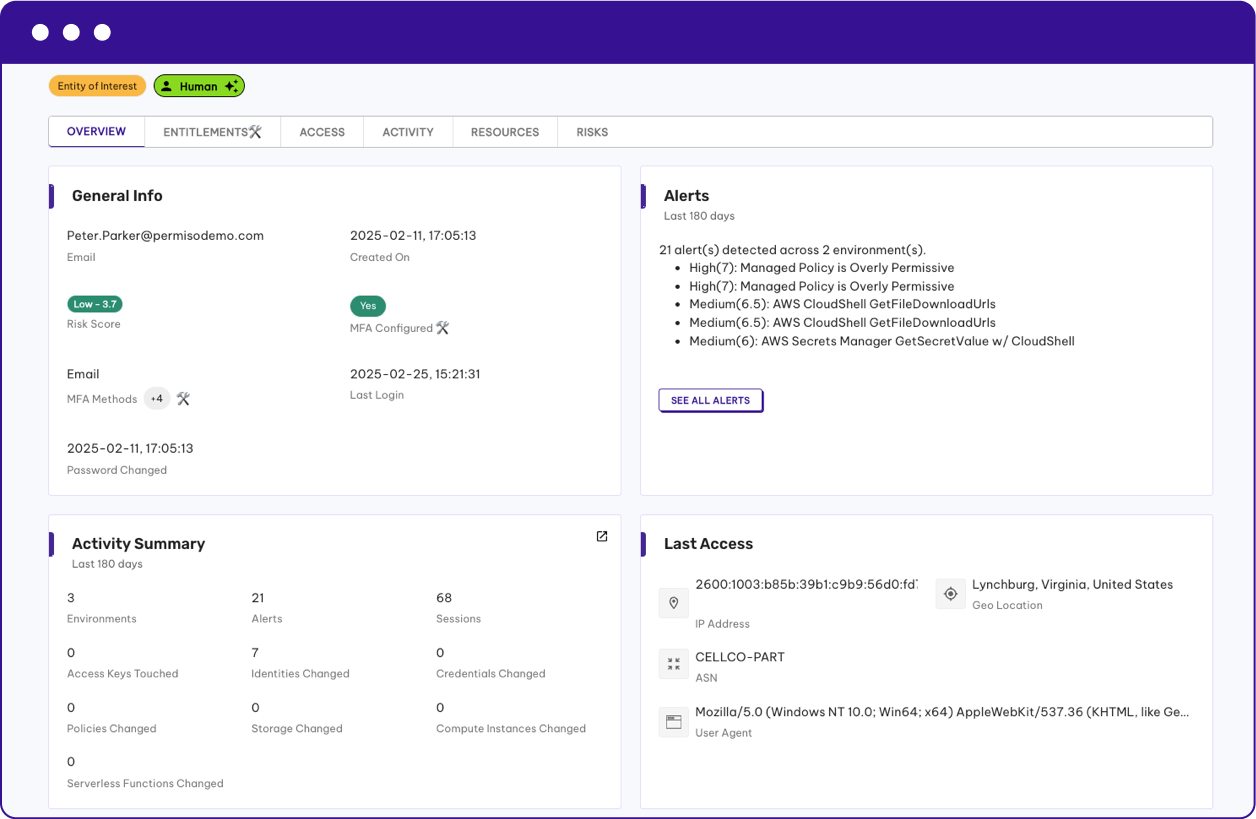
How Permiso Detects Identity-Based Threats



Permiso has proven to be indispensable to the way we manage and secure identities across multiple cloud environments.

Permiso's ability to track identities and their activities across Iaas, Saas and identity providers at runtime is unlike any of our existing solutions.


Identity is the silver bullet in the cloud. If you don't get it right, you're dead!




Get in Touch
Request a demo, get more deets, or just say hi.




.png)


